Virus Info
Users tend to call every malicious program a virus, but the dangerous programs encountered these days are rarely viruses in the technical sense. More commonly, they are worms or Trojan horses. The general name for malicious software is malware.
Don't open any attachments! (unless you were expecting to receive one from that person and unless you have scanned the file for viruses.)
Anti-Virus Software / Anti-Malware Software
- A Complete Guide for Removing Malware From Your PC
- How to never accidentally run Malware: Must Have Windows Tweaks - YouTube
- How to Properly Scan Your Computer for Malware
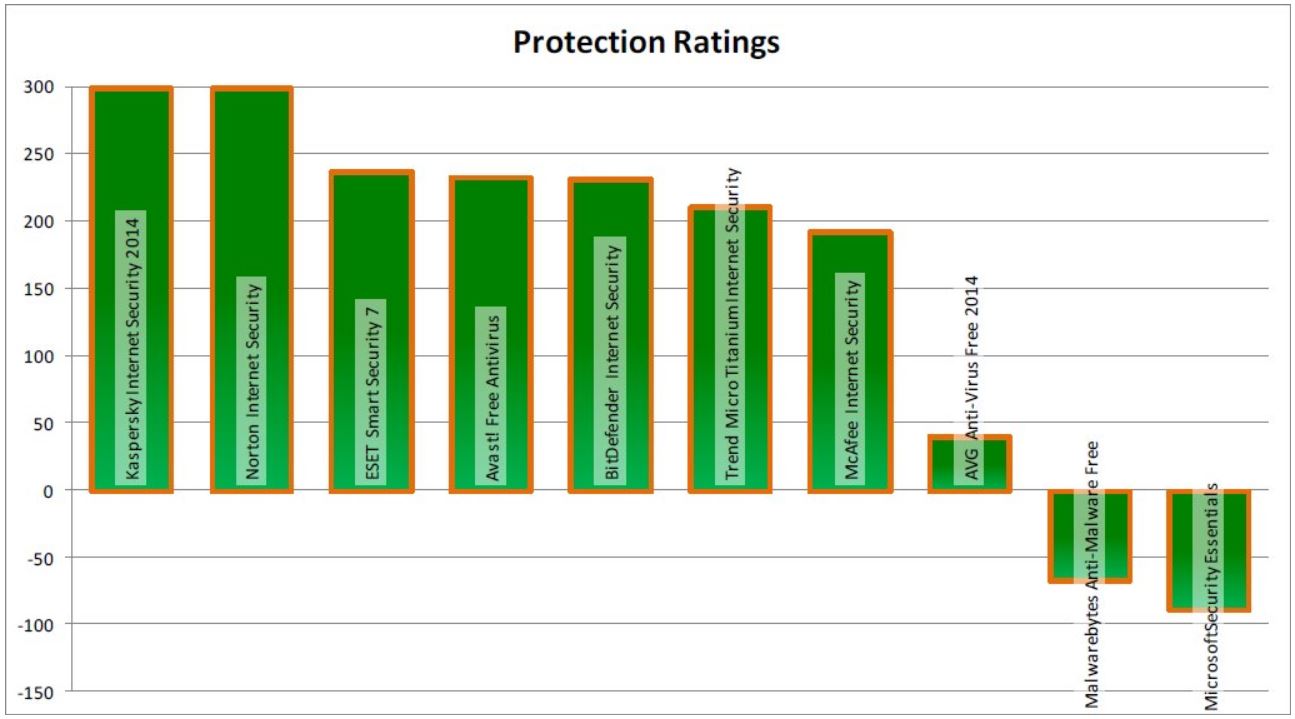
- What is the best antivirus? — The PC Security Channel - thepcsecuritychannel.com
- MakeUseOf - How Accurate Are These 4 Big Name Virus Scanners? - Recommendations (in order):
- Free Online Virus Scan Websites - Not good. Avoid all online virus scan Websites
- AV-Comparatives Comparatives & Reviews - Good, but does not evaluate all common anti-virus products.
- Comodo Firewall
- PCMag
-
- Proton - Privacy by default
- Recommended Anti-Malware
- Not Recommended Anti-Malware
- Avast! - Download antivirus software for spyware and virus protection - $0
or Premium.$100/3PCs
- Avira AntiVir - Antivirus, firewall, antispam, recovery security for Linux, Windows and more
- Kaspersky Antivirus (AVP) Home, virus scanner, software, alerts ... (US$90.MultiDevice)
Kaskpersky - is Russian and is definitely NOT recommended - AVOID Kaspersky- Warning! - Global Office - 39A/2 Leningradskoe Shosse Moscow, 125212 Russian Federation
- kaspersky.com has server problems
- Commerce Department Prohibits Russian Kaspersky Software for U.S. Customers | Bureau of Industry and Security - 2024-06-20
- FCC flags Kaspersky, Russian cybersecurity firm, as national security risk
- Buy Kaspersky Software | Kaspersky Lab Canada
- Kaspersky Internet Security - Free software downloads and reviews - CNET Download.com
- Kaspersky | Antivirus Protection & Internet Security software - Not free - $$ - a Russian company
- Pango Group taking over Kaspersky Lab's U.S. antivirus market after ban - 2024-09-05
- UltraAV by Kaspersky (Pango / Aura - VPN360, OVPN, Betternet, Hotspot Shield, UltraVPN, Avira, Comparitech reviews)
- You can't uninstall it. After a reboot, the program automatically reinstalls itself.
- Urgent!! - Uninstall Kaspersky’s software. Delete all its files still on your machine, even if they’re currently dormant. Uninstall UltraAV.
- McAfee AntiVirus
- Other Anti-Malware
Virus Alerts
- Don't open any attachments! (unless you were expecting to receive one from that person and unless you have scanned the file for viruses.)
- What is fileless malware and how do you protect against it? - TechRepublic
- Ransomware virus scam
- Beware Ransomware | PCMag
- While it is colloquially known as ransomware, the virus is called Reveton. It's designated as a drive-by—catchable by just visiting a compromised site.
Reveton works with the Citadel malware platform, which can install other malware so that even after Reveton is removed, keystroke loggers can capture usernames, passwords, and credit card information.
- The malware often announces itself in a pop-up and (wrongly) informs a computer user that their machine has been commandeered by law enforcement for illegal activity. It will not be unlocked, the message says, until a fine is paid. The announcement looks real, but there may be spelling mistakes.
- Do not pay anything! If you pay, you will be asked to pay even more. (MoneyPack/GreenDot, Ucash/PaySafeCard/SmartVoucher, PayPal, etc.)
These criminals will never unlock your computer, no matter how much you pay. Do not contact the crooks.
- rootkits
- Solutions
- DO NOT switch off your computer normally, just hold down the power button or switch it of at the wall.
- Press F8 key while booting. This should bring up the black screen asking if you want it in safe mode. Select 'safe mode with networking'.
- Try to do a system restore to an earlier point in time. (System restore probably won't fix the problem, but it has worked for some people.)
- Remove the hard drive and plug it into another PC as a USB drive, then use an anti-virus program (Norton) to scan it as an external drive.
- Bootable CD solutions:
- Attempt cleanup using a bootable rescue CD, something that many security vendors supply for free. Of course, you'll have to download and burn the CD on a clean system.
- Bootable USB solutions:
- FixMeStick Review | PCMag - boots into its own Linux installation and handles scanning for malware automatically; you don't have to interact until you give it permission to clean up what it found.
- HitmanPro 3.7 | PCMag - is specifically designed to fight ransomware.
- Reformat the boot drive. Reinstall the operating system. Since you always do regular backups, you can simply retrieve your data from your backup.
- Heartbleed virus/bug
- Mydoom - Wikipedia - W32/Mydoom@MM
- MyDoom worm spreading fast, Worm creates possessed zombie army to attack SCO website,
The MyDoom worm can make a zombie of your computer
The MyDoom worm (also known as Novarg or Mimail-R) spreads via email, using a variety of technical-sounding subject lines and attachment names. If the attached file is launched, and the worm activated, the infected computer's hard disk is harvested by the worm for more email addresses to send itself to. The worm opens a backdoor onto infected computers which allows hackers to gain access.
The worm also spreads via the KaZaA file sharing network, and launches a denial of service (DoS) attack from infected computers (known as "zombies") against SCO's website.
"MyDoom is unlike many other mass-mailing worms we have seen in the past, because it does not try to seduce users into opening the attachment by offering sexy pictures of celebrities or private messages," said Graham Cluley, senior technology consultant for Sophos. "MyDoom can pose as a technical-sounding message, claiming that the email body has been put in an attached file. Of course, if you launch that file you are potentially putting your data and computer straight into the hands of hackers."
"When the MyDoom worm forwards itself via email, it can create its attachment in either Windows executable or Zip file format. It is possible the worm's author did this in an attempt to bypass company filters which try and block EXE files from reaching their users from the outside world," continued Cluley.
- Blaster (msblaster.exe)
- Just being online is enough to get this worm. It doesn't require you to make the mistake of opening an e-mail attachment.
- Buffer Overrun In RPC Interface Could Allow Code Execution (823980). Originally posted: July 16, 2003
- Windows Update: FAQ - Windows Help - Be sure to reboot your system after installation is complete. Installing the patch is the preferred solution, but if that's not possible, block TCP/UDP ports 4444, 135, 139, and 445 at the firewall to help prevent external exploitation of this vulnerability.
- Comments
- service = server (e.g. Web server = HTTP server)
- ports = sockets
- Nimba Worm - Microsoft TechNet (admiN)
- Viruses are often delivered with e-mail attachments. Even if you know the sender, the attachment may contain a virus. You must keep your virus protection software data files up-to-date and always scan all attachments. An even safer (but extreme) solution is to refuse to open any e-mail attachment.
- E-mail Attachments commonly use these filename extensions to spread viruses:
- *.bat, *.com, *.exe, *.pif, *.scr, *.vbs, *.doc, etc...